views
Let us begin
You see this trendy expression 'Cyber Security' all over. However, is that for the most part present to it? No! Like the wide range of various areas of IT, Cyber Security has its sorts. You can't just say that you need to secure your organization's information. There, you have an application, cloud arrangement, correspondence channels, endpoint gadgets, and to wrap things up the organization. Along these lines, you need to secure your framework in all layers. This blog will walk you through the various kinds of Cyber Security and dangers that you need to pay special mind to. Want to learn more? Enrol in this Cyber Security course in Bangalore now to learn more. Let us move ahead in this blog and learn more about Cyber Security.
What is Cyber Security?
Cyber safety is a bunch of practices that assist organizations with ensuring PC frameworks, network gadgets, and projects from cyberattacks. It is identified with data security, and the two terms are utilized reciprocally now and again.
This field is getting progressively pertinent because of the world's immense dependence on the Internet for everything. It accompanies huge intricacies because of quick mechanical development and an outstanding number of cyberattacks. An astounding piece of information (University of Maryland) uncovers that programmers assault at regular intervals, which makes Cyber Security a significant test in the contemporary world.
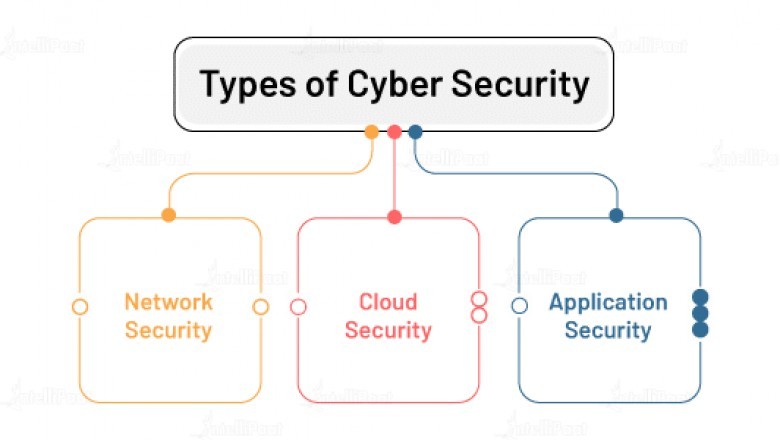
Types of Cyber Security
Cyber safety is only an umbrella term that contains different layers of safety endeavours to get information from digital dangers. How about we have a glance at the sorts of Cyber Security in this part.
Network Security
As the name recommends, in network security you need to forestall noxious/unapproved clients from getting inside the organization. This is significant to stay with a's trustworthiness, unwavering quality, and ease of use set up. You need to painstakingly screen the approaching and active traffic inside the organization. In addition, to guarantee secure exchange of information, you ought to have all imperative programming introduced, including firewalls, hostile to infection, VPN, against spyware, IPS, and so forth to forestall cyberattacks.
Application Security
Any application you dispatch in the market is consistently defenceless to cybercrimes as it will experience various end-clients and different partners and, thus, face the enhancement of the organization. In this manner, you need to ensure the information you store on the application data set from the individuals who approach your application. You should in this manner utilize different devices and techniques to give controlled admittance to your application and its information. You ought to likewise get the application during the turn of events and organization stages.
Cloud Security
Moving the on-premises information to the cloud is the pattern now as IT organizations are attempting to lessen their operational expenses. This implies, rather than a conventional, secure stack, clients are presently associated on the web, which opens them to programmers. This postures you with the need to guarantee security between the client and the cloud supplier. Likewise, you need to assume responsibility for IAM clients. Rivalling the current requests from the business, the notable cloud suppliers, for example, AWS, GCP, and Azure are prepared to furnish you with a protected framework.
Concluding
We are about to finish this blog, and, ideally, you have discovered this asset to be well-improving your comprehension of the sorts of Cyber Security and the types of Cyber Security dangers. As innovation advances, step by step, you will experience all the more new digital dangers, so it is quintessential for you to stay up with the latest about the arising dangers to adapt to and shield against unlawful programmers.












