views
When it comes to your organization's information security management system (ISMS), it's important to have a high-risk tolerance. This means being willing to take on and manage risk in order to protect your data. Keep reading to learn how to ensure that your information security system has a high-risk tolerance.
Protecting Your Information Assets
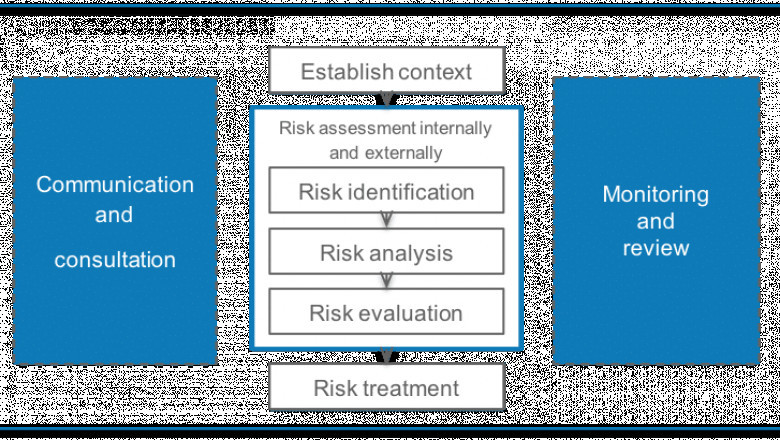
An organization's ISMS is its backbone for protecting its information assets. However, if an organization's ISMS has a low-risk tolerance, it will be less likely to implement effective controls that protect its assets. Conversely, if an organization's ISMS has a high-risk tolerance, it will be more likely to implement effective controls that protect its assets. ISO 27001 risk assessment is the process of identifying, assessing, and managing information security risks to an organization. The main purpose of a risk assessment is to identify potential threats and vulnerabilities that could impact the confidentiality, integrity, or availability of information assets. Once the risks have been identified, they need to be assessed in order to determine their severity and likelihood of occurrence. This will help you to prioritize your risks and determine which ones need to be addressed first. Mitigation strategies can then be put in place for those high-priority risks.
Implementing Tailored Controls
After assessing your current security posture, it is important to implement tailored controls that are specific to your organization's needs. These controls should align with your organization's risk appetite and help reduce any potential risks posed by unauthorized access or malicious activity. By following these steps, you can ensure that your system has a high risk tolerance and is better equipped to protect your assets from harm.
Training Employees on Protecting Company Information
An organization's IS management system should have a high risk tolerance in order to be effective. This means that the system should be designed to protect the most sensitive and critical information first. Employees need to be trained on how to protect company information, including how to identify and report potential risks. They should also be aware of the consequences of violating the organization's security policies.
Testing Incident Response Plans Regularly
IS management systems need to have a high risk tolerance in order to be effective. Another way to ensure this is by regularly testing and incident response plans. By doing so, you can identify any areas where your system may be vulnerable and fix them before they become a problem. Additionally, having an effective incident response plan in place can help you quickly and effectively respond to any security incidents that may occur.
Implementing Comprehensive Information Security Management Processes
Another step to ensure your ISMS has a high risk tolerance is to create an information security framework that will guide the implementation of the policy. The framework should include detailed procedures for identifying and assessing risks, implementing controls, and monitoring and reviewing performance. It's also important to establish lines of responsibility and reporting structures so that everyone in the organization understands their role in safeguarding sensitive data. Finally, it's essential to put into place effective training and awareness programs so that employees are aware of their responsibilities when it comes to protecting company data. Employees must understand how to identify potential threats and take appropriate steps to mitigate them. Regular training and reinforcement is critical in order to maintain a high level of awareness throughout the organization.
Overall, it is important to have a high-risk tolerance when implementing an information security management system in order to ensure that the system is able to protect against potential cyber-attacks. Without a high-risk tolerance, the system may be too conservative and not able to adapt to new and evolving threats.












