views

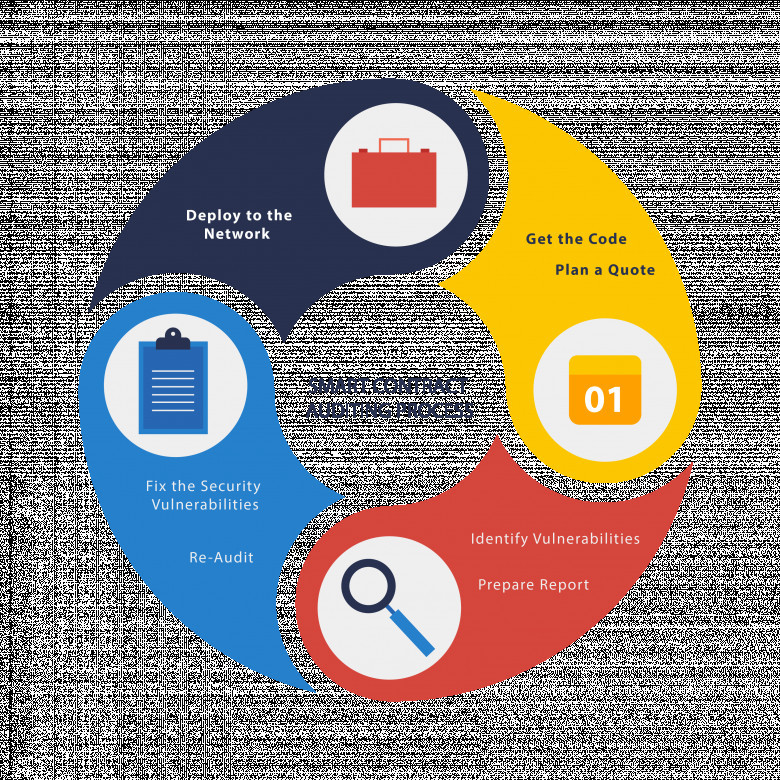
A smart contract audit follows a very standard procedure and can differ significantly between smart contract auditors. The following is a typical procedure:
Collection of code design models
To ensure guaranteed integration of third-party smart contracts, auditors collect code specifications and examine the architecture. This helps auditors understand the objectives of the project and determine its scope.
Run Unit Tests
Auditors then test cases to test each smart contract feature. Audit specialists use tools (both manual and automated) to ensure that unit test cases include the general code of the smart contract.
Select Audit Approach
Since manual auditing is more efficient than automated auditing, auditors often inspect smart contracts without the help of software. Attacks like front-running can be effectively recognised using this method.
Write the Initial Report
After the audit is complete, the auditors write up the discovered code flaws and provide feedback to the project team to fix those bugs. Some smart contract service providers have a team of experts who help fix every bug found.
Publish the Final Audit Report
Once the errors are corrected, the auditors publish the final report, taking into account the actions taken by the project team or external experts to solve the problems that were raised.
Key Vulnerabilities in Smart Contracts
In this section, common security flaws in smart contracts are described.
Timestamp Dependency
The smart contract execution environment is on the miner's side, unlike typical programs. When the logic of a contract depends on the current time, the miner can manipulate the current time to influence the execution outcome and meet a predetermined goal.
Feature Visibility Errors
The default visibility property of a function in Solidity is public. Anyone can access a private function if a developer forgets to specify the visibility of that function. For instance, anyone can immediately void the contract by calling the Destruct method.
Reentry Attacks
One of the most devastating attacks on the Solidity smart contract is the reentrancy attack. A developer's indifferent attitude can potentially lead to re-entry issues. When a function makes an external call to another contract that is not trusted, it is called a re-entrancy attack. Then, in an attempt to drain funds, the untrusted deal makes a recursive call to the original function.
Random Number Vulnerability
An attacker can accurately guess the random number generated by a contract using a publicly known variable as a seed.
Failure to differentiate between humans and contracts
It may have unintended consequences if it is unclear whether the caller of the smart contract is a person or a contract. For example, by correctly guessing the block in the popular game Fomo3d, a hacker can earn money through the airdrop function (ie by accurately predicting the timestamp of a contract).
Spelling Mistakes
Constructors are commonly used for contract initialization and to determine the owner of the contract. The compiler would not notice the misspelling of the function during programming, which would result in the function being public so anyone can call it.
A function is used to set a contract's state variables in Solidity. When a contract is first built, the function is called and can be used to set initial values. Public and internal constructors are the two different categories. Additionally, Solidity code is compiled using a Solidity compiler, which produces bytecode and other artifacts necessary for smart contract implementation.
Consider the case when the HelloWorld contract function is misspelled as Helloworld; any user can call the Helloworld function to change the owner of the contract.
Recent Cyberattacks on Blockchain/Smart Contracts
Recent events show that the smart contract as a blockchain technology is not immune to cyber-attacks and exploiting vulnerabilities:
In 2017, $150 million worth of ETH was stolen from an organization called Parity technologies due to a critical vulnerability present in their Ethereum smart contract.
In 2016, a DAO called the Genesis DAO was compromised by a hacker who took advantage of a security breach in the system. Hackers here stole ETH valued at $50 million from Genesis DAO crowdfunding participants.
One of the biggest cryptocurrency thefts happened in August 2021. Hackers stole $613 million worth of digital currency from a company called the Poly Network. They exploited vulnerability in the digital contracts used by the Poly Network.
Conclusion
A smart contract security audit is necessary today to protect your contracts from external attacks. The audit is done by others, but it is essential that they are reverified by the actual contractors, who verified the actual flaws in the project. Through the audit, both parties will be able to understand smart contracts more deeply. It is essential that all people who want to invest in smart contracts evaluate their auditing measures so that their transactions are secure.












